OpenVPN GP4 (en): Unterschied zwischen den Versionen
Mfgeg (Diskussion | Beiträge) K |
Mfgeg (Diskussion | Beiträge) K |
||
| Zeile 9: | Zeile 9: | ||
* In '''Bridge''' mode a virtual network interface (tap0) is created, which is connected over a network bridge (br0) with the internal network adapter (eth0) of the Dreambox. One or more OpenVPN clients get an IP address of the internal network and can access all available services without additional routing. | * In '''Bridge''' mode a virtual network interface (tap0) is created, which is connected over a network bridge (br0) with the internal network adapter (eth0) of the Dreambox. One or more OpenVPN clients get an IP address of the internal network and can access all available services without additional routing. | ||
| − | * In '''Tunnel''' Mode the client only has a connection to the OpenVPN server of the Dreambox. A virtual IP will be assigned for each client according to the subnet (10.128.0.0/24) which is defined in the server configuration. The OpenVPN server uses the IP address <code>10.128.0.1</code>. Access to the internal network is not possible by default, but can be enabled by IP forwarding and routing. | + | * In '''Tunnel''' Mode the client only has a connection to the OpenVPN server of the Dreambox. A virtual IP will be assigned for each client according to the subnet (<code>10.128.0.0/24</code>) which is defined in the server configuration. The OpenVPN server uses the IP address <code>10.128.0.1</code>. Access to the internal network is not possible by default, but can be enabled by IP forwarding and routing. |
==== Requirments for the usage ==== | ==== Requirments for the usage ==== | ||
Version vom 8. Oktober 2018, 23:08 Uhr
After the installation of the plugin, an easy configurable OpenVPN Server or Client is available. The OpenVPN uses certificates used for Servern-Multi-Client setups and an encrypted TLS connection.
The OpenVPN Server can be configured for Bridge (tap) or Tunnel (tun) Mode.
- In Bridge mode a virtual network interface (tap0) is created, which is connected over a network bridge (br0) with the internal network adapter (eth0) of the Dreambox. One or more OpenVPN clients get an IP address of the internal network and can access all available services without additional routing.
- In Tunnel Mode the client only has a connection to the OpenVPN server of the Dreambox. A virtual IP will be assigned for each client according to the subnet (
10.128.0.0/24) which is defined in the server configuration. The OpenVPN server uses the IP address10.128.0.1. Access to the internal network is not possible by default, but can be enabled by IP forwarding and routing.
Inhaltsverzeichnis
Requirments for the usage
- OpenVPN Server must be configured and startet.
- The OpenVPN Server only supports wired network (no WLAN).
- Portforwarding on the router towards the Dreambox (port 1194/UDP)
- To connect to the Server, the WAN IP must be known, or a DDNS Service should be configured (e.g. No-IP).
- Certificates need to be created for each client (OVPN Package).
- OpenVPN needs to be installed on all clients. Protocols such as IPSec, IKE, PPTP, or L2TP are not supported.
- Server LAN and Client LAN must be different.
OpenVPN Server
Configure the OpenVPN Server as follows:
Configure OpenVPN Server
- Start the OpenVPN Server plugin.
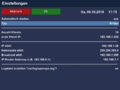
- Select the required Mode and the amount of clients with MENU → Settings. When using the Bridge Mode, an IP Range for the clients can be set. If the OpenVPN Server should be available after a reboot of the Dreambox, enable the setting Start Automatically.
Create Certificates
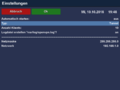
Open the certificate settings with the yellow button. Add with the green button the following certificates:
- Root certificate. Define a password, validity period ... as wanted.
- Server certificate. Enter the previously defined password and the validity period.
- Finally the User certificate will be created. Enter the previously defined password and the validity period and a name for the client.
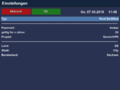
Create OVPN Package for the client
Open the certificate setting with the yellow button. Select the different clients and create the OpenVPN archives with the yellow button. The archive contain the configuration files and certificates, which will be needed to setup the clients. The zip archives are saved in:
/etc/ssl/openvpn
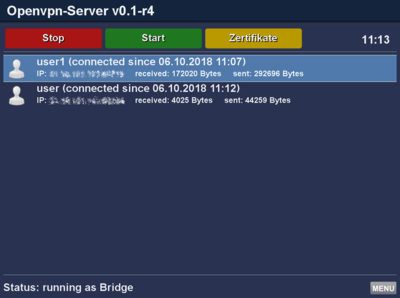
Start / Stop the OpenVPN Server
Start the OpenVPN Server with the green button. red stops the OpenVPN Server.
Additional informations
- Configuration files and certificates of the OpenVPN Server are saved in
/etc/openvpn. - When the OpenVPN Server is running, the menu Settings is not available.
- Connected clients will be visible after an interval of 60 seconds.
- Use the MENU button to display a log file.
OpenVPN Server Screenshots
OpenVPN Client
OpenVPN Client Screenshots
Block certifikates
Certificates can be blocked, to disable the connection from a client. Open the certificate settings with the yellow button and select the client you want to block. Disable the certificate with the red button.