SSH (en): Unterschied zwischen den Versionen
(→Aufruf) |
Mfgeg (Diskussion | Beiträge) |
||
| (8 dazwischenliegende Versionen von 2 Benutzern werden nicht angezeigt) | |||
| Zeile 3: | Zeile 3: | ||
|[[Bild:english.png]] - [[SSH (en)|in English]] | |[[Bild:english.png]] - [[SSH (en)|in English]] | ||
|} | |} | ||
| − | ''ssh'' stands for ''Secure Shell''. This is not a Shell as we know it, but a secure tunnel through an unsecure network. The most known unsecure network is the internet. For a safe communication the proven [http://en.wikipedia.org/wiki/Cryptography| Public/Private Key Process] is used, because the password should also be transfered in a secured way over the network. Because this | + | '''''ssh''''' stands for ''Secure Shell''. This is not a Shell as we know it, but a secure tunnel through an unsecure network. The most known unsecure network is the internet. For a safe communication the proven [http://en.wikipedia.org/wiki/Cryptography| Public/Private Key Process] is used, because the password should also be transfered in a secured way over the network. Because this asymmetric encryption (different keys for encrypting and decrypting) requires a lot (too much) processor time, the encryption will switch automatically to a symmetric encryption (same key for encrypting and decrypting) once the connection is made. The key is changed and negotiated each time again. |
It's recommended to avoid unencrypted [[Telnet (en)|Telnet]]- (or [[FTP (en)|FTP]]-) connections, and the use of secure ssh connections is preferable. The shell on the remote computer can be used similar in both cases. In the actual connection the user will not notice any difference using the unsecure telnet or secure ssh. | It's recommended to avoid unencrypted [[Telnet (en)|Telnet]]- (or [[FTP (en)|FTP]]-) connections, and the use of secure ssh connections is preferable. The shell on the remote computer can be used similar in both cases. In the actual connection the user will not notice any difference using the unsecure telnet or secure ssh. | ||
| Zeile 19: | Zeile 19: | ||
=== Windows Client === | === Windows Client === | ||
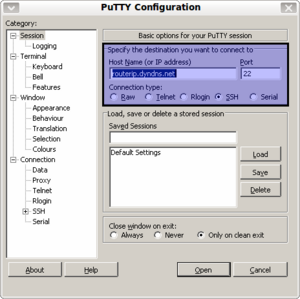
| − | For connecting from a local Windows computer with the Dreambox, [[PuTTY|Putty]] is an nice | + | For connecting from a local Windows computer with the Dreambox, [[PuTTY|Putty]] is an nice program. |
| − | == | + | == Licence == |
| − | + | For licence reasons most of the Linux Distributions don't use the original ''ssh'', but the free ''open ssh''. But this offers the same functions and is no problem for using with the Dreambox. | |
| − | == | + | == Interesting Links == |
| − | * [[Dropbear]] | + | * [[Dropbear (en)|Dropbear]] the SSH Server of the Dreambox. |
| − | * | + | * Secure copying with [[SCP (en)|SCP]]. |
| − | * | + | * Detailed article [http://en.wikipedia.org/wiki/Secure_Shell SSH on Wikipedia]. |
| − | + | * Windows Client Programm: [http://www.putty.org Putty]. | |
| − | |||
| − | |||
| − | * Windows | ||
[[Kategorie:Basics_(en)]] | [[Kategorie:Basics_(en)]] | ||
| − | [[Kategorie: | + | [[Kategorie:Network (en)]] |
[[Kategorie:Enigma2 (en)]] | [[Kategorie:Enigma2 (en)]] | ||
[[Kategorie:Enigma (en)]] | [[Kategorie:Enigma (en)]] | ||
Aktuelle Version vom 12. November 2016, 17:23 Uhr
ssh stands for Secure Shell. This is not a Shell as we know it, but a secure tunnel through an unsecure network. The most known unsecure network is the internet. For a safe communication the proven Public/Private Key Process is used, because the password should also be transfered in a secured way over the network. Because this asymmetric encryption (different keys for encrypting and decrypting) requires a lot (too much) processor time, the encryption will switch automatically to a symmetric encryption (same key for encrypting and decrypting) once the connection is made. The key is changed and negotiated each time again.
It's recommended to avoid unencrypted Telnet- (or FTP-) connections, and the use of secure ssh connections is preferable. The shell on the remote computer can be used similar in both cases. In the actual connection the user will not notice any difference using the unsecure telnet or secure ssh.
Inhaltsverzeichnis
Connecting
Preparation
Linux Client
Opening a Shell from the local Linux computer can be done as follows:
ssh root@ip_der_dreambox
Windows Client
For connecting from a local Windows computer with the Dreambox, Putty is an nice program.
Licence
For licence reasons most of the Linux Distributions don't use the original ssh, but the free open ssh. But this offers the same functions and is no problem for using with the Dreambox.
Interesting Links
- Dropbear the SSH Server of the Dreambox.
- Secure copying with SCP.
- Detailed article SSH on Wikipedia.
- Windows Client Programm: Putty.