SSH (en): Unterschied zwischen den Versionen
| Zeile 3: | Zeile 3: | ||
|[[Bild:english.png]] - [[SSH (en)|in English]] | |[[Bild:english.png]] - [[SSH (en)|in English]] | ||
|} | |} | ||
| − | ''ssh'' stands for ''Secure Shell''. This is not a Shell as we know it, but a secure tunnel through an unsecure network. The most known unsecure network is the internet. For a safe communication the proven [http://en.wikipedia.org/wiki/Cryptography] is used, because the password should also be transfered in a secured way over the network. Because this asymetric encryption (different keys for encrypting and decrypting) requires a lot (too much) processor time, the encryption will switch automatically to a symetric encryption (same key for encrypting and decrypting) once the connection is made. The key is changed and negociated each time again. | + | ''ssh'' stands for ''Secure Shell''. This is not a Shell as we know it, but a secure tunnel through an unsecure network. The most known unsecure network is the internet. For a safe communication the proven [http://en.wikipedia.org/wiki/Cryptography| Public/Private Key Process] is used, because the password should also be transfered in a secured way over the network. Because this asymetric encryption (different keys for encrypting and decrypting) requires a lot (too much) processor time, the encryption will switch automatically to a symetric encryption (same key for encrypting and decrypting) once the connection is made. The key is changed and negociated each time again. |
It's recommended to avoid unencrypted [[Telnet (en)|Telnet]]- (or [[FTP (en)|FTP]]-) connections, and the use of secure ssh connections is preferable. The shell on the remote computer can be used similar in both cases. In the actual connection the user will not notice any difference using the unsecure telnet or secure ssh. | It's recommended to avoid unencrypted [[Telnet (en)|Telnet]]- (or [[FTP (en)|FTP]]-) connections, and the use of secure ssh connections is preferable. The shell on the remote computer can be used similar in both cases. In the actual connection the user will not notice any difference using the unsecure telnet or secure ssh. | ||
Version vom 16. August 2013, 20:39 Uhr
ssh stands for Secure Shell. This is not a Shell as we know it, but a secure tunnel through an unsecure network. The most known unsecure network is the internet. For a safe communication the proven Public/Private Key Process is used, because the password should also be transfered in a secured way over the network. Because this asymetric encryption (different keys for encrypting and decrypting) requires a lot (too much) processor time, the encryption will switch automatically to a symetric encryption (same key for encrypting and decrypting) once the connection is made. The key is changed and negociated each time again.
It's recommended to avoid unencrypted Telnet- (or FTP-) connections, and the use of secure ssh connections is preferable. The shell on the remote computer can be used similar in both cases. In the actual connection the user will not notice any difference using the unsecure telnet or secure ssh.
Inhaltsverzeichnis
Aufruf
Vorbereitung
- Es muss per Telnet ein Passwort für den Benutzer root gesetzt werden.
- Dropbear Dienst muss aktiv sein.
Linux Client
Der Aufruf von einer Shell des lokalen Linux-Rechners aus auf die Dreambox sieht dann so aus:
ssh root@ip_der_dreambox
Windows Client
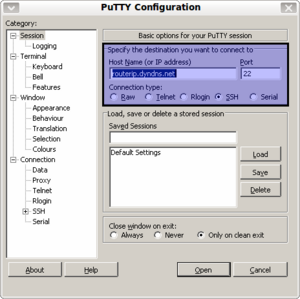
Zum Aufruf von einem lokalen Windows-Rechner aus auf die Dreambox ist das Programm Putty sehr interessant.
Lizenz
Aus lizenzrechtlichen Gründen wird bei den meisten Linux-Distributionen nicht das ursprüngliche ssh eingesetzt, sondern die freie Variante der open ssh. Von den Funktionen her ist das aber zu vernachlässigen und auf der Dreambox nicht relevant.
Literaturhinweise
- Dropbear der SSH Server der Dreambox.
- Sicheres kopieren mit SCP.
- Nutzung der secure shell lt. Wikiartikel SSH Tunnel zum Webif erstellen.
- "Sicher senden", ein Artikel des Magazins "Linux-User".
- Umfangreicher Artikel der Wikipedia.
- Unterforum Sicherheit von linuxforen.de.
- Windows-Client-Programm: Putty.